Azure Key Vault
Microsoft Key Vault: A Comprehensive Overview
What is Azure Key Vault?
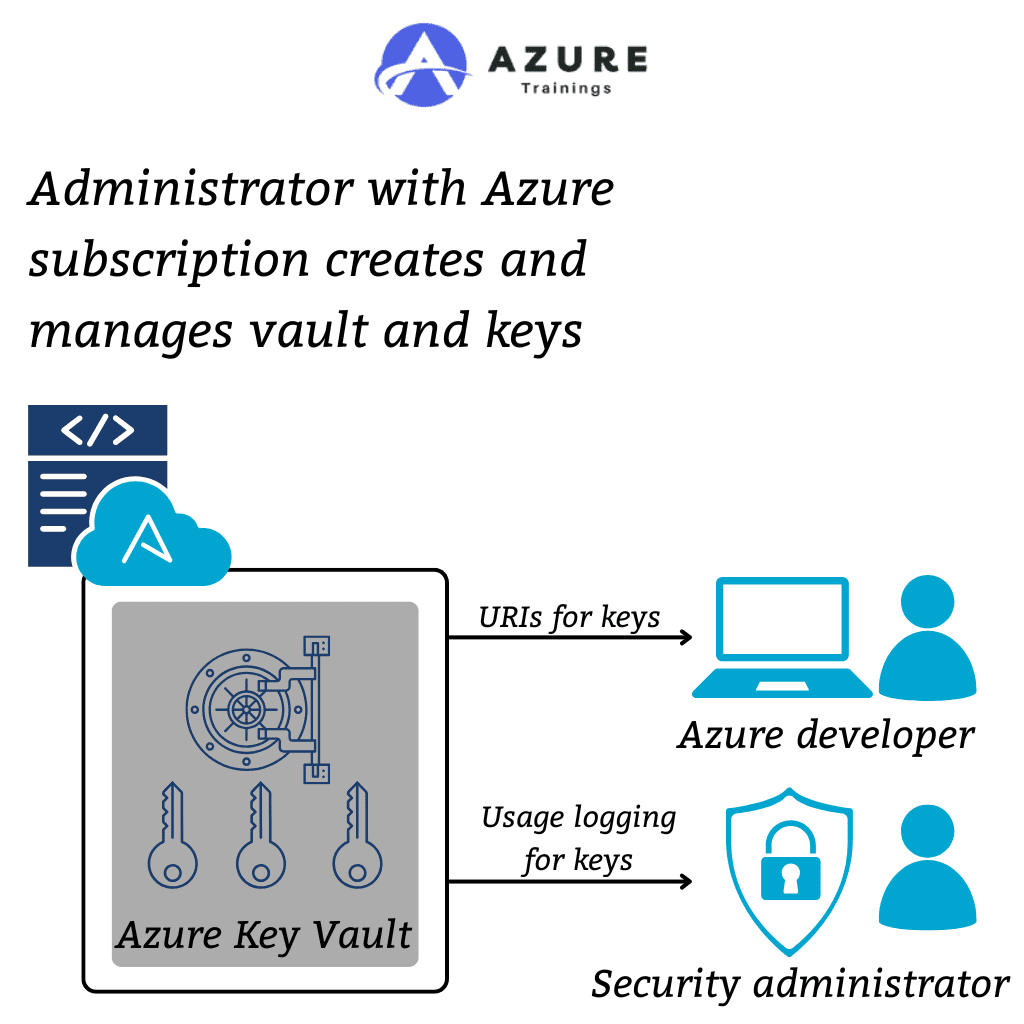
- Microsoft Key Vault is a cloud-based service that enables organizations to securely store and manage sensitive data, such as cryptographic keys, passwords, connection strings, and digital certificates.
- In simpler terms, it’s a safe place in the cloud where you can keep secrets that are critical to your applications and systems.
- When you develop or maintain an application, you often need to handle sensitive information. For instance, you might need a password to access a database or an API key to interact with another service.
- Storing these secrets securely is essential, as exposure to unauthorized access can lead to security breaches. Key Vault helps you do this in a way that minimizes the risk of exposing sensitive data.
- Apart from just storing secrets, Key Vault also provides secure management, access control, and monitoring of these sensitive assets. With the use of Key Vault, you do not have to store critical secrets in your code or on local servers, which greatly reduces the chance of accidental exposure
Azure Key Vault Overview
- This allows Key Vault to serve as a central vault for securely storing and managing cryptographic resources such as keys, secrets, and certificates.
- That way, instead of having your secrets strewn about in different locations like configuration files, databases, or even hard-coded within your code, it all resides securely in one location.
- The integration of Key Vault with Azure Active Directory, an identity and authentication service of Azure, implies that access to Key Vault is identity-based, thereby governing who is allowed access to the keys, secrets, and certificates that are stored there. Only the right users, applications, or services with correct permissions will gain access to this.
- Azure Active Directory will ensure sensitive data is accessed only by people and systems who need it most.
- With Key Vault, fine-grained access control can be implemented, whereby users and services have different permissions, depending on the role that the user has taken.
- In the security architecture of your system, it is thus necessary to restrict which parts can view sensitive data only to what’s necessary.
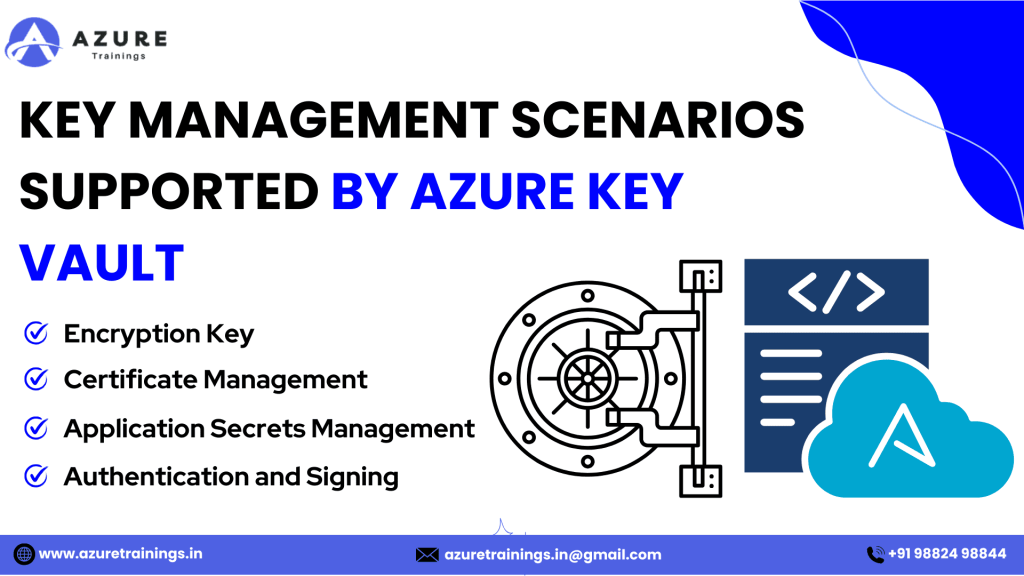
Key Management Scenarios Supported by Azure Key Vault
- Key Vault is a highly versatile service, which supports multiple key management scenarios. These key management scenarios enable organizations to securely manage sensitive information, including encryption keys, application secrets, digital certificates, and even authentication credentials.
- Here is a detailed explanation of the key management scenarios supported by Key Vault:
1. Encryption Key Management
- Encryption keys are one of the major applications of Key Vault. With the most modern cloud application, it has become a significant requirement to protect data with encryption.
- Encryption ensures that even if the intercepted or illegal users access the data, it will not be readable for them without the proper decryption key. Key Vault lets organizations store and manage their respective cryptographic keys used for encrypting and decrypting data.
- Virtual Machines (VMs): Virtual machine deployment in Azure makes use of encryption keys in protecting data in a VM. The Key Vault can secure such keys from being accessed unless authorized users or services request the access.
- Storage Accounts: Storage accounts contain sensitive information in the form of customer details, financial statements, and personal documents. At rest, this information is encrypted. Encryption keys can be stored within these storage accounts for Key Vault to handle the lifecycle, like rotation or expiration of those keys.
- Databases: Another important use case is database encryption. Be it Azure SQL Database, Cosmos DB, or any other database service, Key Vault can manage the encryption keys required to protect the data stored within them
2. Certificate Management
- The primary use of digital certificates is in securing communication between different systems or services, especially when those communications need to be encrypted.
- Key Vault provides secure certificate management, which is important for securing your data in transit.
- SSL/TLS Certificates: A web application establishes a secure connection with its users by using SSL/TLS certificates when using HTTPS. These certificates are used to ensure that the data is encrypted as it travels between the web server and user. Key Vault will store them, manage the lifecycle (including renewals), and will allow only the authorized services to use these certificates.
- Signing Certificates : In some contexts, digital certificates are used in signing content to confirm its integrity and authenticity. Take, for example, code-signing certificates in ensuring that one’s software was not tampered with. It can store signing certificates securely as well as help manage them from Key Vault.
3. Application Secrets Management
- Application secrets are sensitive data, such as API keys, connection strings, passwords, and other information that applications require to function. Instead of having them directly in code or configuration files, which is risky, Key Vault provides a secure, centralized location for storing these secrets.
- API Keys: Many web applications or services interact with third-party APIs that require authentication via API keys. Developers can ensure that the keys are never exposed in the code and are only accessible by the authorized applications or services by storing these keys in Key Vault.
- The connection strings are used to connect an application to a database, a messaging queue, and other services. Storing the connections in Key Vault will encrypt them and manage access in a secure way, thus risking accidental exposure.
- Passwords: The storing of passwords inside an application or configuration file is a serious security risk. Key Vault lets organizations store application passwords securely for more controlled accessibility, say, for example, being accessible to only the web server or database.
4. Authentication and Signing
- In addition, Key Vault is essential in authentication and signing operations for cloud-based applications. These scenarios are important to validate the identity of users, services, or systems and to ensure that transactions or data exchanges are legitimate and secure.
- Authentication: Key Vault is integrated with Azure Active Directory (AAD) for authenticating users, services, and applications. Using managed identities allows services or virtual machines to access Key Vault securely without the need to hard-code credentials within the application. This means only authorized entities will be able to access sensitive information stored in the Key Vault.
- Signing Transactions: In cloud-based applications, signatures are usually used to validate the authenticity and integrity of transactions or messages. Key Vault can store cryptographic keys used for signing digital transactions (such as JSON Web Tokens – JWTs or other forms of tokens). These signatures prove that a transaction or message originated from a trusted source and has not been tampered with.
- Verifying Transactions: In addition to signing, A Key Vault can be used for verifying the origin of transactions or messages. Since public keys that are used to verify are stored and managed by organizations, this ensures that any incoming data was signed by a party authorized to do so
Why These Scenarios Matter in Key Vault
- Each of these key management scenarios is critical for securing modern applications, databases, and services. Without proper management of encryption keys, certificates, application secrets, and authentication processes, organizations are exposed to sensitive data exposure, security breaches, or failure to meet regulatory compliance standards.
- Azure Key Vault mitigates such risks through the provision of a secure, centralized system for handling these critical components, automating key rotations, forcing access controls and giving strong integration with other services in Azure.
- You’re managing a small application or an enterprise-level system, Key Vault protects your sensitive data and grants its access to only authorized users and service
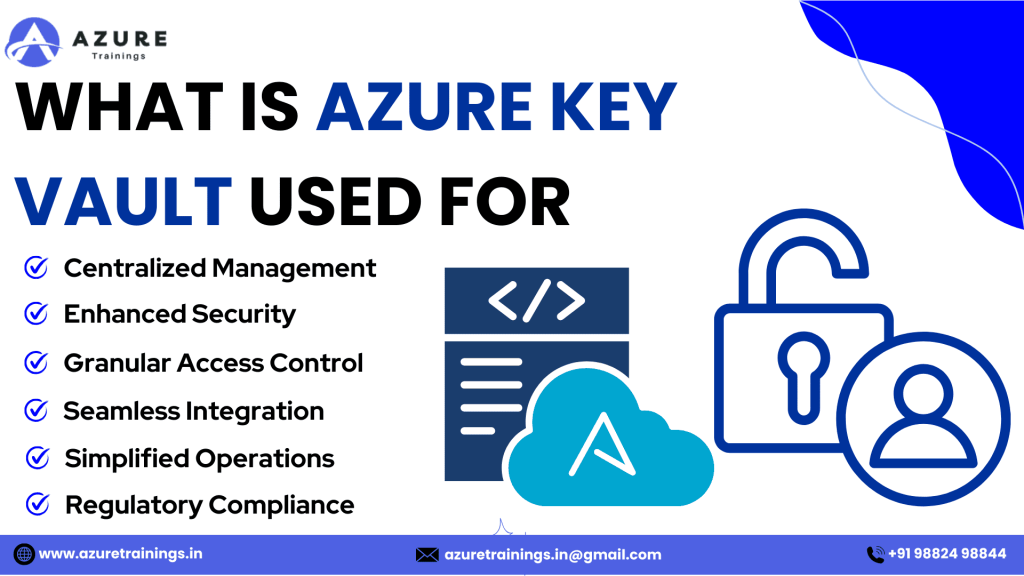
what is azure key vault used for
- Key Vault is a powerful service that offers many benefits to organizations, especially in managing sensitive data like encryption keys, secrets, and certificates.Here are more detailed explanations of these benefits:
1. Centralized Management
- One of the prominent strengths of Key Vault is the offering of centralized management for all cryptographic assets, which include keys, secrets, and certificates.
- Since sensitive data would not have to be distributed or scattered across various systems, databases, or applications, there exists a single, secure location provided by Key Vault, where all those critical resources are accumulated and managed.
- This centralization provides an easy management and monitoring for access to the sensitive information that is always kept secure and up-to-date.With Key Vault, organizations can streamline their data management practices, reduce redundancy, and simplify the overall process of managing sensitive assets
2. Enhanced Security
- Security is one of the most vital aspects of any cloud service. Key Vault ensures that all your sensitive data is protected to the highest level. Key Vault uses hardware security modules (HSMs) for key storage, providing another layer of security through the storing of keys in physical hardware devices designed specifically for secure cryptographic operations.
- These HSMs are tamper-resistant, protect your keys against unauthorized access and malicious attacks.Additionally, Key Vault ensures that its data is encrypted both at storage and transmission whether in the vault or while traveling to an authorized user or service.Enhanced protection from data breach, unauthorized accesses, and a whole host of security threats happens in this sense.
3. Granular Access Control
- Azure Key Vault allows for fine-grained access control, such that you could determine the very precise permissions around who could get access to any specific key, secret, or certificate.Only the right set of users, services, or applications would get access to your sensitive data.For instance, you can have different access levels for different users in your organization.
- For example, you could give administrators full control over the Key Vault, while developers or other users only have read-only access.
- This way, you can ensure that sensitive information is not exposed to anyone who does not need it, following the principle of least privilege.With Azure Active Directory integration, roles and permissions are easily set according to identities for users so that access could be managed simply
4. Seamless Integration
- Key Vault integrates nicely with other Azure services and platforms.Whether you are using Azure Virtual Machines (VMs), Azure Kubernetes Service (AKS), Azure App Service, or any other Azure service, Key Vault can securely store and provide access to secrets, certificates, and encryption keys that those services need to function.
- For example, you can store database connection strings in Key Vault, and your applications running on Azure App Service can securely retrieve them when needed.The integration with Azure Active Directory ensures that these services can access the necessary secrets without requiring hardcoded credentials, making it easier to build and scale secure cloud-based applications.
5. Simplified Operations
- Key rotation, expirations, and even lifecycle management can be complex to deal with when managing cryptographic assets.However, Key Vault automates most of these tasks, thus greatly minimizing manual intervention on keys and secrets, as well as ensuring that they are always up to date.
- For instance, Key Vault can automatically rotate encryption keys and reduce the likelihood of keys getting compromised over time.You can also set the expiration dates of secrets and certificates so that they are renewed or replaced before becoming outdated.Such automation simplifies operations, saves time, and reduces human errors, ensuring your system remains secure and compliant without further effort.
6. Regulatory Compliance
- Many organizations are concerned about compliance with industry standards and regulations, especially when dealing with sensitive data.Key Vault assists organizations in meeting a variety of regulatory compliance requirements, including data security, encryption, and access control.
- For instance, it has support for the use of industry-standard encryption algorithms and such important features like key versioning and auditing, ensuring Key Vault to meet any compliance standards as may be applied from GDPR to HIPAA and all the rest in between including PCI-DSS.
- By using Key Vault, organizations would be able to ensure that all regulatory requirements relating to data protection are met by maintaining a secure and compliant infrastructure.
- Overall, Key Vault offers a robust and secure solution for the management of sensitive data, streamlines operations, and ensures industry regulations are complied with.Through the central management of encryption keys, secrets, and certificates; improved security by the use of HSM-backed storage; granular access control; and seamless integration with other Azure services, Key Vault allows organizations to better protect their data while streamlining key management processes.
- Whether you’re protecting your cloud infrastructure, automating main tasks of the lifecycle management, or meeting regulatory requirements, Key Vault can be that aid to ensure that the data is safe and manageable.
Azure Key Vault Pricing

- Azure Key Vault provides flexible pricing plans to address different use cases and organisational needs.Here are the basis on which the pricing is structured, which includes the type of tier, the quantity of keys, secrets, and certificates that you wish to store and the number of operations that you conduct.Here’s the elaboration on the pricing detail:
1. Standard Tier Pricing
- The Standard Tier suits general-purpose uses where you don’t need the greatest security or niche features.It charges less for storage and key and secret management as compared to Premium.This level is generally okay for most usual use cases.
- For example, it is the best place for storing application secrets, connection strings, or other encryption keys with virtual machines and storage accounts.
- In the Standard Tier, the pricing is on:The number of secrets, keys, or certificates
- That are being stored: The number of resources that you will have to pay for in a Key Vault.A charge for every secret, key, or certificate added.Operations are incurred each time a key, secret, or certificate is created, updated, or accessed.Such operations as getting a secret or updating a key are chargeable based on how often the operations are carried out.
- The Standard Tier offers a more economical option for those businesses that just require simple key and secret management without HSMs or any other advanced feature
2. Premium Tier Pricing
- The Premium Tier is for those organizations that require an advanced level of security and added features, like HSMs, which are designed to store keys.This tier allows for the more advanced capabilities needed to manage sensitive cryptographic assets.It’s especially suitable for finance, healthcare, or government-related services, which have stringent needs for data protection.
- The following are the details of Premium Tier pricing:HSM-backed keys: In this tier, the keys are stored in HSMs, providing more security than software-based encryption.HSMs are specialized physical devices specifically designed to manage and safeguard cryptographic keys.
- Advanced features: Premium Tier also has features like key versioning that helps manage easier rotations of the keys and improved monitoring and auditing capabilities to keep track of who accessed your vault and when.
- Higher costs based on usage: In general, Premium Tier costs are higher than that of Standard Tier because of added security features and infrastructure.Prices in this tier are usage based, that is, depending upon the number of keys, secrets, and certificates stored, along with the operations performed on the resources.
- For instance, if your organization handles sensitive information or is bound by very stringent regulatory requirements, the Premium Tier ensures that your keys are safely stored and managed according to the highest standards of cryptographic asset protection
3. Factors Affecting Azure Key Vault Pricing
Several factors determine the cost of Key Vault use:
- Number of resources stored: The more keys, secrets, and certificates you store in your Key Vault, the more it will cost.This is because each resource stored incurs a charge.
- Operations performed : Key Vault charges for all operations related to your keys, secrets, and certificates.Any creation, updation, fetching, or even deletion of resource incurs charge.The number of operations you’re performing will give you the bill frequency.
- Advanced features: Any advanced features like HSM-backed keys or the enabling of logging and monitoring can be charged separately.These additional features enhance security and auditing but increase the total cost.
- Vaults and regions: The cost may vary based on the region of Azure in which your Key Vault is located.Some regions may have different pricing based on local infrastructure costs or availability of feature
4. Additional Costs to Consider
While Key Vault’s core pricing is based on storage and operations,there may be additional costs related to:
- Access policies: If your Key Vault needs complex access control configurations or it is integrated with other Azure services, such as Azure Active Directory for managing access, there could be additional operational costs related to identity and access management.
- Monitoring and auditing: If you use advanced monitoring or set up logging for audit purposes, these features might incur extra costs.The pricing for Key Vault is designed to offer flexibility, ensuring that businesses of all sizes can securely manage their cryptographic assets at a cost-effective price.
- The Standard Tier is for more general use at a lower price, and the Premium Tier adds advanced security capabilities, such as HSM-backed keys, to scenarios where additional levels of protection are needed.By paying for resources you store and operations you perform, you can tailor your Key Vault usage to fit the specific needs and budget of your organization
Key Vault: Components, Features, and Best Practices
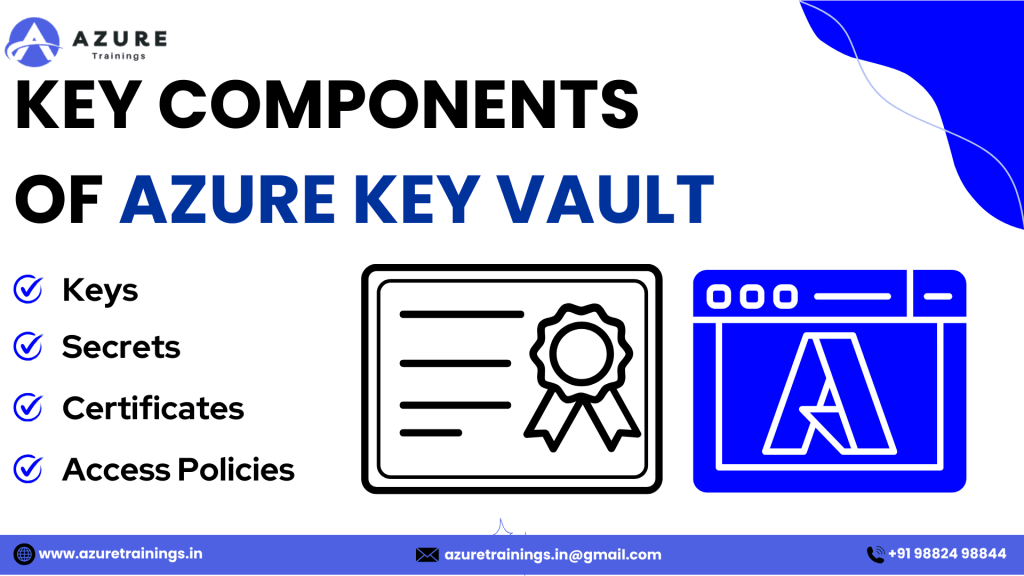
Key Components of Azure Key Vault
Key Vault is composed of several core components that help in managing cryptographic assets and ensuring data security.Each of these core components is described below:
- Keys: Keys are the cryptographic resources used for encryption, decryption, signing, and verification operations.These keys help protect sensitive data and ensure its confidentiality and integrity.Keys can be used for encrypting data stored in Azure services, such as virtual machines, storage accounts, or databases.
- Secrets: This is sensitive information such as a password, an API key, or a connection string that you want to store safely and manage properly.Key Vault lets you store these secrets in an encrypted format and retrieve them programmatically.By storing secrets in Key Vault, you avoid exposing secrets in application code or configuration files.
- Certificates: Certificates are used to secure communications over networks. Key Vault helps manage and store digital certificates used for establishing secure connections between services, websites, and users.For example, SSL/TLS certificates used in HTTPS communication can be stored and managed in Key Vault.
- Access Policies: Access policies define who can access the Key Vault and specify which actions they are allowed to perform.These policies control access to the stored keys, secrets, and certificates, ensuring that only authorized users or applications can retrieve or modify these sensitive assets.Access policies are managed using Azure Active Directory (AAD) identities.
Features of Azure Key Vault
- Key Vault provides a myriad of powerful features, which give the product credibility as a sound, secure option for cloud storage of sensitive information.
- It securely stores sensitive data using advanced encryption algorithms for data stored at rest as well as in transit.Data held within the vault is encrypted; hence only permitted entities can have access to such data, preventing it from falling into the wrong hands.
- Access Control: Key Vault uses Azure Active Directory (AAD) to provide role-based access control (RBAC).This allows organizations to define roles for users and applications, restricting access to sensitive resources based on those roles.For example, only specific users or services may be granted permission to access certain secrets or keys.
- Key Lifecycle Management: Key Vault simplifies managing cryptographic keys throughout their lifecycle.It supports automation around key generation, storage, rotation, and expiration.This way, the operations of maintaining security in keys over time can be automated rather than doing it manually.
- Monitoring and Auditing: Key Vault provides robust logging and auditing capabilities.It keeps detailed records of every activity that pertains to the vault, for example, access logs on who accessed a specific secret, when, and what actions were performed.All these logs enable organizations to maintain a proper check on usage, detect unauthorized access, and guarantee compliance with the security policies.
- Integration: Key Vault integrates with all other Azure services, such as Azure Functions, Azure App Service, and Azure Storage.This enables developers to build secure applications that automatically retrieve secrets, certificates, and keys from the vault without exposing sensitive information in code.
Best Practices for Using Azure Key Vault
- To make full use of Key Vault, and to be sure that your sensitive data stays safe, the following best practices are to be followed:
- Use Managed Identities: Instead of hardcoding credentials or secrets directly in your application code, use Azure Managed Identities for secure authentication.Managed Identities provide an identity for applications that can be used to access Azure resources without requiring explicit credentials to be stored in code or configuration files.This eliminates the risk of exposing sensitive information.
- Rotate Keys Regularly: To enhance security, set up automated key rotation policies.Key rotation ensures that encryption keys are updated periodically, making it harder for attackers to exploit compromised keys. Key Vault can automate key expiration and replacement processes, reducing manual overhead and minimizing security risks.
- Implement Least Privilege Access: When creating access policies, follow the principle of least privilege.This involves granting only the minimum necessary permissions to users, applications, or services.Doing so reduces the risk of unauthorized access or accidental modification of sensitive resources.Monitor Usage.Access to Key Vault should always be monitored regularly through logs and audit trails.Configure alerts so that any kind of unusual activity, such as users or services gaining unauthorized access to keys or secrets, can be spotted.Monitoring and auditing are one of the crucial elements in tracking possible security breaches before they might do any harm.
- Azure Key Vault: An Essential Service for Secure Scalable Management of Cryptographic Keys, Secrets and Certificates, is an in-depth understanding about the key constituents, leveraging on its powerful functionality, and keeping best practices under its usage.Organizations need to ensure safeguarding their data in the cloud by using their sensitive data.Therefore, centralization of key management and access control in Key Vault can mitigate the risk from data breaches enormously and simplify critical resource security in complexity
how to create azure key vault
- Key Vault is a versatile tool designed to securely manage cryptographic keys, secrets, and certificates. Here’s a step-by-step guide on how to use Key Vault effectively:
- Step 1: Create a Key Vault
- Creating a Key Vault is the first step in using the service. You can create a Key Vault in several ways:
- Azure Portal: The Azure Portal provides a user-friendly interface where you can easily create and manage resources, including Key Vaults. You simply navigate to the Key Vault service, click on “Create,” and then specify the details like the vault’s name, region, and access policies.
- Azure CLI: If you prefer a command-line interface, Azure CLI allows you to create a Key Vault using commands. This is particularly useful for automation or scripting purposes. The command typically involves defining parameters such as the vault name, location, and access policies.
- Terraform: For Infrastructure-as-Code (IaC) users, Terraform enables the automated creation of Key Vault resources. This is beneficial when you need to manage and provision infrastructure consistently across environments, ensuring scalability and repeatability.
- When creating the vault, it’s important to define:
- Vault Name: A unique name that identifies the Key Vault.
- Region: The geographical location where the vault is created, which affects data residency and access latency.
- Access Policies: Access control settings that define who can access the vault and what actions they can perform (e.g., read, write, delete). This is done using Azure Active Directory identities.
- Step 2: Create and Manage Cryptographic Assets
- Once your Key Vault is set up, you can start storing and managing sensitive data within it. Here’s what you can do:
- Store Encryption Keys: You can store keys that are used for encrypting and decrypting data. These keys can be used to protect stored data in Azure services or secure communications between services.
- Store Secrets: You can store sensitive information like API keys, database connection strings, or passwords. Secrets are encrypted and securely stored, and you can retrieve them when needed by your applications.
- Manage Certificates: Digital certificates, often used for secure communications (e.g., SSL/TLS certificates), can also be stored and managed in the Key Vault. This helps protect the integrity and security of your communications.
- Generate or Import Keys: You can generate new cryptographic keys within Key Vault or import existing keys from external sources. Key Vault also supports key rotation, meaning you can periodically change your keys to maintain security.
- Configure Access Policies: You can define detailed policies that specify which users, applications, or services can access or modify your keys, secrets, and certificates. This ensures that only authorized entities can interact with your sensitive resources.
- Step 3: Manage Access to the Key Vault
- Access control is critical when using Key Vault. You need to define who has access to the resources stored in the vault and what they can do with them. Key Vault uses two primary methods for managing access:
- Azure Role-Based Access Control (RBAC): RBAC allows you to assign roles to users, groups, or applications within Azure Active Directory (AAD). Roles define the level of access granted. For example, a user might be granted the “Reader” role to view secrets, but not to modify them.
- Access Policies: In addition to RBAC, you can configure access policies that define the specific operations that users or applications can perform on the Key Vault’s contents. You can set permissions for each type of asset (keys, secrets, certificates) and for different actions (e.g., create, delete, read).
- By managing access carefully, you ensure that only authorized users or applications can access the sensitive data stored in the vault. You can also implement the principle of least privilege, granting only the permissions necessary for each user or service.
- Step 4: Monitor and Audit Activity
- Monitoring and auditing are essential components of ensuring security and compliance in Key Vault. Azure provides built-in tools to help you track and analyze activity related to your Key Vault:
- Azure Monitor Integration: Key Vault integrates with Azure Monitor to log activity and usage within your vault. You can track actions such as who accessed the vault, what resources they accessed (keys, secrets, certificates), and when the access occurred.
- Logging and Alerts: Logs are generated for every action performed in Key Vault, including read and write operations. These logs can help you identify any unauthorized or suspicious activity. You can set up alerts based on certain criteria, such as when a user accesses a sensitive secret or performs an operation that’s outside the normal behavior.
- Audit Trails: Key Vault provides an audit trail of all activity, allowing you to ensure that all actions are in compliance with your organization’s security policies and regulations. This helps demonstrate adherence to industry standards for data protection and governance.
Ways to Create a Key Vault in Azure
- There are several methods available for creating a Key Vault in Azure, each catering to different needs and preferences. Whether you prefer a visual interface, command-line automation, or Infrastructure-as-Code (IaC), Azure provides flexible options to choose from
- Terraform is an Infrastructure-as-Code (IaC) tool that allows you to define, provision, and manage Azure resources using code. With Terraform, you can automate the creation and configuration of Key Vault, making it especially useful for large or complex deployments where consistency is crucial.
- Benefits:
- Automation: You can script and automate the creation and management of Key Vaults, reducing manual intervention.
- Consistency: Since everything is defined in code, you can ensure that the Key Vault is created with the same configuration every time, even across multiple environments (e.g., development, staging, production).
- Version Control: The code can be stored in version control systems like Git, providing a history of changes and the ability to revert to previous configurations if needed.
- Scalability: Terraform makes it easy to scale your infrastructure by defining resources as code, allowing you to deploy multiple Key Vaults across different regions and environments.
- Example: Here’s a simple Terraform script to create a Key Vault in Azure:
provider “azurerm” {
features {}
}
resource “azurerm_key_vault” “example” {
name = “example-keyvault”
location = “East US”
resource_group_name = “example-resources”
sku_name = “standard”
2. Using Azure CLI
- The Azure Command-Line Interface (CLI) provides a powerful set of commands for managing Azure resources directly from the terminal or command prompt. It’s ideal for users who are comfortable with command-line tools or need to automate tasks via scripts.
- Benefits:
-
- Efficiency: Azure CLI commands allow you to quickly create and manage Key Vaults without needing to navigate through a graphical interface.
-
- Scripting: You can automate resource creation by embedding Azure CLI commands into scripts, which is especially useful in DevOps pipelines or when provisioning resources across multiple environments.
- Integration: Azure CLI can easily be integrated into continuous integration/continuous deployment (CI/CD) workflows, enabling faster deployment cycles and better scalability.
- Customization: You can modify and configure your Key Vault and its resources in real-time, giving you more flexibility to adjust configurations as needed.
- Example: Here’s a basic command to create a Key Vault using Azure CLI:
> az keyvault create –name “example-keyvault” –resource-group”example-resources” –location “East US”
3. Using Azure Portal
- The Azure Portal is a web-based graphical user interface (GUI) that provides an intuitive, user-friendly environment for managing Azure resources. It is well-suited for beginners or those who prefer a visual approach to resource management.
- Benefits:
- Ease of Use: The Azure Portal offers a simple, point-and-click interface for creating and managing Key Vaults, making it the best choice for users who prefer visual guidance over text-based commands.
- Real-Time Feedback: As you interact with the portal, it provides instant feedback, showing available resources, settings, and configurations, making it easier to understand what’s happening.
- Visual Management: It’s easy to navigate through your resources and quickly find and manage Key Vaults along with other Azure resources. You can view logs, set permissions, and configure other aspects of the Key Vault directly through the GUI.
- Steps to Create a Key Vault:
- Sign in to the Azure Portal.
- Search for “Key Vault” in the search bar and select the Key Vault service.
- Click “Create,” then fill in the required details, such as the vault name, region, and resource group.
- Configure access policies and permissions for the vault, then click “Create” to provision the Key Vault.
Accessing Azure Key Vault
- Key Vault is designed to securely store and manage sensitive information, and it provides several methods for applications and services to access that information.Here, we’ll look at how different platforms, like Azure Virtual Machines (VMs) and Azure Kubernetes Service (AKS), can securely interact with Key Vault.
1. Key Vault from Virtual Machines (VMs)Azure Virtual Machines (VMs)
- Azure Virtual Machines(VMs) can use secrets from Key Vault without the application code being forced to include hard-coded values like passwords or connection strings.It’s achieved using Managed Identities and Azure SDKs.
- Azure Resources with Managed Identities: Instead of using shared service identities that provide an identity to the virtual machine to access various Azure services including Key Vault, application credentials are used that are managed at the resources rather than hard coded in code and stored at multiple places or are exposed directly to the users and applications running within the infrastructure.
- How it works: When you enable a managed identity for a VM, the VM can authenticate to Key Vault and retrieve secrets securely.Access to the Key Vault is controlled by Azure Role-Based Access Control (RBAC) and Key Vault access policies, so only authorized users or services can access the data.
- Azure SDKs: Azure SDK (Software Development Kit) provides libraries and tools that help make it easy to connect an application running in a VM with Key Vault.SDKs can be used to securely retrieve secrets, certificates, and keys from the vault.
- Example: An application running on a VM can use the SDK to authenticate through a managed identity to gain access to a secret in Key Vault without having to manage credentials themselves.
- Security: Exposure of sensitive credentials is avoided by not maintaining them within the code and ensuring that the secrets aren’t leaked.
- Convenience: Authentication can be made very convenient through managed identities, as this avoids the management of credentials.Complies with the standards for best secure storage and access of secrets for the applicatio
2.Accessing Key Vault from Azure Kubernetes Service (AKS)
- Azure Kubernetes Service, also known as AKS, is a managed service that enables the running of containerized applications in Azure.In this regard, AKS and Key Vault can be combined to enable access to secrets from the Key Vault by Kubernetes applications without exposing the same in plain text.
- Integration with Kubernetes Secrets: AKS can integrate with Key Vault by using Kubernetes secrets.Kubernetes Secrets are objects that store sensitive information like passwords, OAuth tokens, and ssh keys.Using the Key Vault Provider for Kubernetes, AKS clusters can fetch secrets directly from Key Vault and inject them into Kubernetes secrets.
- How it works: The Key Vault provider enables AKS clusters to automatically create Kubernetes secrets from Key Vault and also to retrieve those secrets.As soon as a secret is put into Kubernetes, it can safely be mounted inside pods or passed securely to the containers.
- Key Vault Provider for Kubernetes: This provider makes it easier for AKS clusters to manage secrets from Key Vault.The provider enables secure retrieval of secrets and injects them into Kubernetes configurations (for example, environment variables or configuration files).
- Secure Secret Management: Avoid storing secrets in Kubernetes configurations or container images, thus minimizing the chance of accidental exposure.
- Simplified Configuration: It integrates Key Vault with Kubernetes seamlessly, allowing developers to access sensitive information securely and efficiently.
- Centralized Management: Key Vault allows for centralized control of secrets across multiple Kubernetes clusters, thereby improving overall security and management
Key Vault Documentation
Microsoft provides detailed documentation on Azure Key Vault, which guides users through understanding, configuring, and troubleshooting the service.The documentation includes:
- Step-by-Step Guides: These guides provide detailed instructions on setting up and using Key Vault, including how to create a Key Vault, manage secrets, and configure access policies.
- Examples are provided to illustrate real-life scenarios where Key Vault can be utilized, such as protecting secrets for cloud-based applications, securing certificates for HTTPS communications, or securing encryption keys for data storage.
- Best practices on the safe and efficient management of secrets within Key Vault can also be garnered from the documentation, including best practices on key rotation, access control, compliance, and others.
- Troubleshooting Resources: The documentation will have solutions to the most common problems so that if a user has a problem, they can quickly troubleshoot and solve it.
- Thorough Learning: Documentation will allow beginners and experts alike to understand how to effectively use Key Vault.Deep Examples: There are practical examples on how to implement and integrate Key Vault in your applications.
- Support: Troubleshooting resources will ensure you can quickly solve any issues you might face while using Key Vault. Key Vault offers applications, either running on Virtual Machines (VMs) or within Azure Kubernetes Service (AKS) clusters, a secure and flexible way to access secrets.This is achieved by the combination of managed identities and Azure SDKs for VMs, in addition to Kubernetes secrets for AKS, which ensures secrets are retrieved securely and used without exposing them in the application code.
- In addition, the whole Key Vault documentation is presented to the customers with guides to detailed best practice and troubleshooting support, thus offering to ensure efficient secure secrets management for compliance with respective industry standards.Now be it application-building on VM, AKS or any other such Azure platform- Key vault simplifies such a process securely managing and also accessing sensitive da
Frequently Asked Questions (FAQs)
Can Microsoft Access the Azure Key Vault?
- No. Key Vault is designed with strict access controls, ensuring that Microsoft cannot access the contents of your vault. Access is controlled entirely by your organization’s policies and identity management.
- Key Vault simplifies the complexities of managing sensitive information, offering organizations a secure and efficient way to safeguard their digital assets.
How Do I Get Started with Key Vault?
- Getting started with Key Vault involves several key steps that help you set up and manage your secure resources in the cloud. Here’s how to begin:
- Create an Azure Account:
- If you don’t have an Azure account, you’ll need to create one. Go to the Azure portal and sign up for an account if you haven’t already.
- Create a Key Vault:
- Once your Azure account is set up, the next step is to create a Key Vault. You can do this using the Azure Portal, Azure CLI, or Terraform. The Azure Portal provides a user-friendly interface, while the CLI and Terraform offer more automation and scripting capabilities.
- Azure Portal: Go to the Azure Portal, navigate to the “Key Vaults” section, click “Create,” and follow the steps. You will need to define a vault name, select the region, and configure access policies.
- Azure CLI: Use the Azure Command-Line Interface (CLI) for creating a Key Vault. You can execute commands like:
bash
Copy code
az keyvault create –name <your-keyvault-name> –resource-group <your-resource-group> –location <your-location> - This will create a Key Vault in the specified resource group and location.
- Configure Access Policies:
- After creating your Key Vault, configure access policies to determine who can access the vault and perform actions such as adding, retrieving, or deleting keys, secrets, and certificates.
- Use Azure Active Directory (AAD) to control access and assign appropriate permissions based on roles.
- Store Secrets, Keys, and Certificates:
- Once your Key Vault is set up and access is configured, you can begin storing cryptographic assets like secrets (e.g., passwords, API keys), encryption keys, and certificates.
- Access Control: Ensure that only authorized applications and users can access these stored resources by setting strict access policies
What Are Some Best Practices for Using Azure Key Vault?
- To make the most out of Key Vault while ensuring maximum security and efficiency, it is important to follow some best practices:
- Use Managed Identities:
- Managed identities for Azure resources help your applications authenticate to Key Vault without needing to store credentials in the application code. This enhances security by avoiding exposure of sensitive credentials.
- Enable Key Vault Logging and Monitoring:
- Always enable logging and monitoring to track who is accessing your Key Vault and what actions are being performed. Azure integrates with Azure Monitor to provide detailed logs of access and usage, which can help detect unauthorized access and ensure compliance.
- Use Azure Active Directory (AAD) for Access Control:
- Leverage Azure Active Directory to control access to the Key Vault. Use Role-Based Access Control (RBAC) to define what actions users and services can perform on keys, secrets, and certificates.
- Implement the least privilege principle by granting only the necessary permissions for users or applications.
- Regularly Rotate Keys and Secrets:
- Implement automatic key and secret rotation to minimize the risk of key compromise. Key Vault offers features like key expiration and automatic rotation to help you manage the lifecycle of cryptographic assets securely.
- Set Up Access Policies:
- Define specific access policies that determine who can access secrets, keys, and certificates. Assign permissions to users, applications, or services with clearly defined roles and actions (e.g., read, write, delete).
- Monitor and Audit Access:
- Regularly audit access logs to check for suspicious or unauthorized access patterns. Monitoring helps identify potential security breaches or compliance issues before they become problematic.
- Integrate with Other Azure Services:
- Key Vault integrates seamlessly with other Azure services, such as Azure App Service, Azure Functions, and Azure Kubernetes Service (AKS). Use these integrations to securely manage secrets and keys within your applications and services.
- Use HSM-Backed Keys for Higher Security:
- If your application needs an extra level of security, consider using Hardware Security Module (HSM)-backed keys. These keys are stored in physical devices that meet high-security standards and are protected from tampering
How Can I Add a Secret to Azure Key Vault?
- Adding secrets to Key Vault is a simple process that allows you to store sensitive information like passwords, API keys, and connection strings securely. Here’s how you can do it:
- 1.Using the Azure Portal:
- In the Azure Portal, navigate to your Key Vault and go to the Secrets section.
- Click + Generate/Import and choose the Add a secret option.
- Enter a name for the secret and the value (the sensitive information you want to store, such as a password).
- Optionally, set activation and expiration dates for the secret.
- Click Create to store the secret in the Key Vault.
- Using Azure CLI:
- You can use Azure CLI to add secrets to Key Vault. Run the following command:
- bash
Copy code
az keyvault secret set –vault-name <your-keyvault-name> –name <secret-name> –value <secret-value> - This command will store the specified secret under the given name in the Key Vault.
- Access the Secret:
- Once added, you can access the secret programmatically through your applications using the Azure SDK, or by using the Key Vault REST API.
- The secret can be accessed securely by applications that have the appropriate permissions configure
How Can I Import Certificates in to Key Vault?
- Importing certificates into Key Vault allows you to securely store and manage them for tasks like SSL/TLS encryption, secure communications, and application authentication. Here’s how you can import a certificate:
- Prepare Your Certificate:
- Make sure you have the certificate file ready, typically in .pfx or .cer format. If your certificate is not in these formats, you will need to convert it using tools like OpenSSL.
- Using the Azure Portal:
- Go to the Key Vault that you want to import the certificate into.
- Under the Certificates section, click + Generate/Import.
- Choose Import as the method for adding the certificate.
- Select the certificate file from your local machine and upload it to the vault. You may need to provide a password for a .pfx certificate.
- Using Azure CLI:
- You can also import certificates via the Azure CLI. For example:
bash
Copy code
az keyvault certificate import –vault-name <your-keyvault-name> –name <certificate-name> –file <path-to-certificate-file> - This command imports the certificate into your Key Vault, where it can be used for secure communication or other cryptographic operations.
- Access and Use the Certificate:
- Once imported, the certificate is stored securely in the vault and can be used in your applications for encryption, secure communication, and more.
- You can reference the certificate from your application code or use it for SSL/TLS encryption on Azure services.




